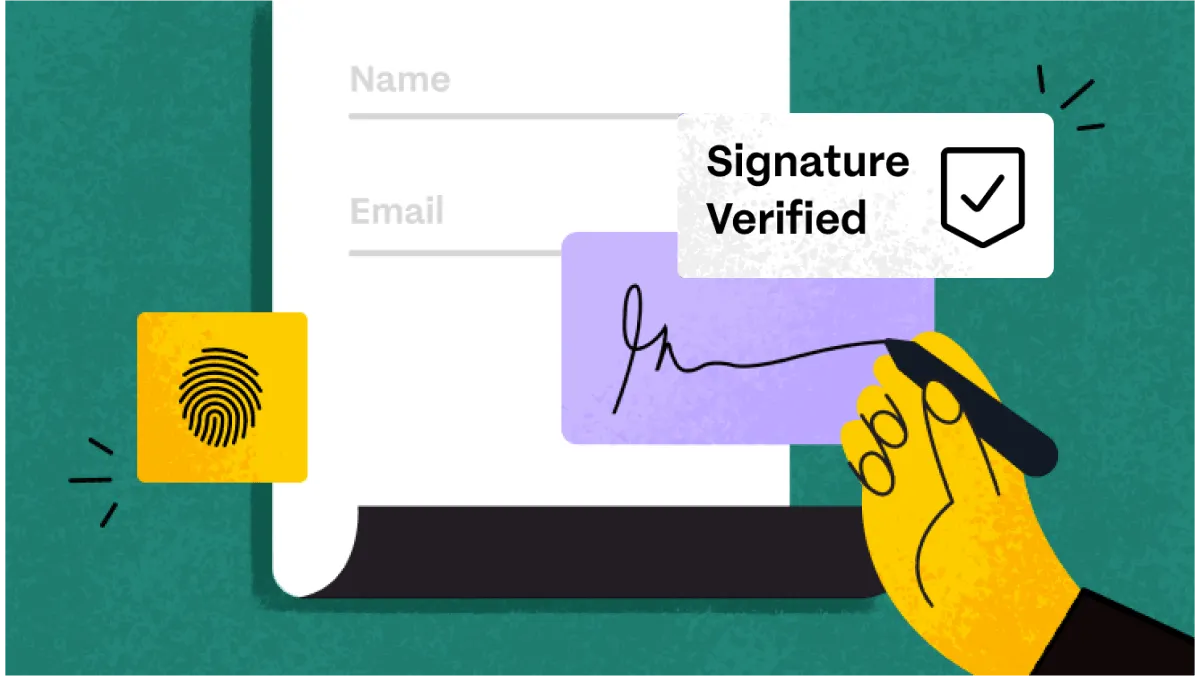
Key Takeaways
- Electronic signatures beat wet signatures in security through encryption, multi-factor authentication, and tamper detection. These features make forgery nearly impossible compared to easily copied handwritten signatures.
- Multiple security layers provide the best protection by combining biometric verification, authentication checks, and encrypted audit trails to make unauthorized access exponentially harder for attackers.
- Security requires ongoing maintenance, not just setup, through quarterly audits, role-based access controls, and vendor oversight to catch vulnerabilities before they become breaches.
- Industries trust eSignatures for high-stakes transactions, with 77% of financial services, 62% of public sector, and 49% of healthcare relying on secure platforms for verified signing.
- Signeasy delivers enterprise-grade security at scale with SOC 2 certification, comprehensive audit trails, digital certifications, SSO logins, role-based access control, and multi-factor authentication that protect documents while accelerating global workflows.
Electronic signatures have become the standard for signing contracts, agreements, and important documents across industries.
But as more organizations and individuals rely on digital signatures for critical transactions, one question keeps coming up. Are electronic signatures really safe?
The short answer is yes — when implemented correctly. Electronic signature security depends on the technology behind it, the platform you use, and how well security measures are followed.
Modern eSignature solutions use advanced encryption, multi-factor authentication, and detailed audit trails to protect your documents and verify signer identity. These security features often make electronic signatures more secure than traditional pen-and-paper (wet) signatures.
In this guide, we’ll cover:
- What electronic signatures are and how they work
- What makes eSignatures secure and trustworthy
- How to identify and prevent common risks
- How to strengthen document security practices
- How organizations use secure electronic signatures today
What are electronic signatures?

Source
An electronic signature, or eSignature, is a digital mark that indicates a person's intent to agree to the content of a document. It replaces the traditional handwritten signature in digital transactions. Today, anyone can create digital signature online using secure platforms that verify identity and protect document integrity.
Electronic signatures can take many forms. They might be a typed name, an uploaded image of your handwritten signature, a click on an "I agree" button, or a signature drawn on a touchscreen device. If you prefer using your own handwriting, learn how to copy signature from image and use it securely across documents.
What’s important isn’t how the signature looks, but that it demonstrates a clear intent to sign and can be linked to the person who signed it.
What makes an electronic signature legally binding?
- In the U.S., the ESIGN Act and Uniform Electronic Transactions Act (UETA) give eSignatures the same legal status as handwritten ones.
- The EU’s eIDAS regulation and India’s IT Act similarly recognize electronic signatures.
- These laws make eSignatures valid for most business and personal documents, from job offers to real estate contracts.
Suggested read: How to create a digital signature
Now that we know what an eSignature is, let’s look at how it really works.
How do electronic signatures work?
Under laws like the U.S. ESIGN Act and the EU's eIDAS regulation, a legally valid electronic signature must demonstrate the signer's intent to sign, be attributable to a specific person, and maintain the integrity of the signed document.
Here's what happens during the signing process:
1. Identity verification
Before you can sign the document, the platform verifies your identity through methods like email authentication, SMS codes, knowledge-based questions, or biometric data.
2. Document encryption
Electronic signature security features encrypt the document during transmission and storage, protecting it from unauthorized access. Digital certificates from trusted certificate authorities provide tamper-evident seals that detect any document modifications. Many users first create their signing mark with an online signature generator so the final signature looks consistent across all documents.
3. Audit trail creation
The platform automatically creates a detailed audit trail that records who signed, when they signed, their IP address, and any authentication methods used.
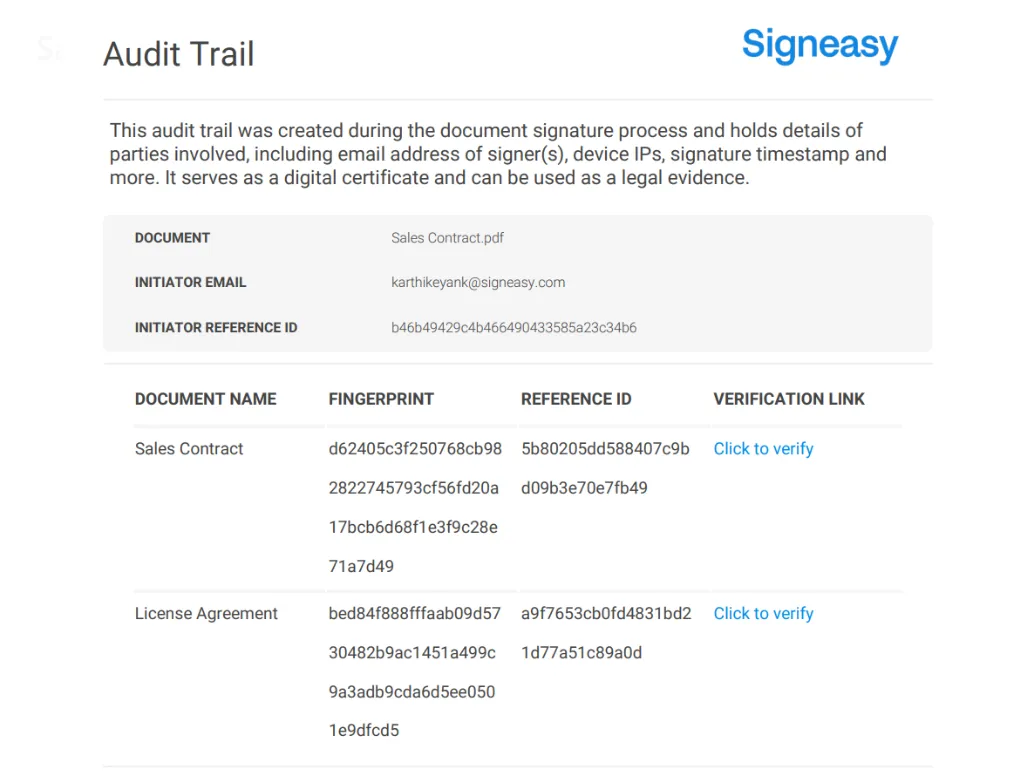
These electronic signature security features work together to create a tamper-evident seal.
4. Certificate binding
Many secure electronic signature solutions use digital certificates to cryptographically bind the signature to both the signer and the document, making any alterations detectable.
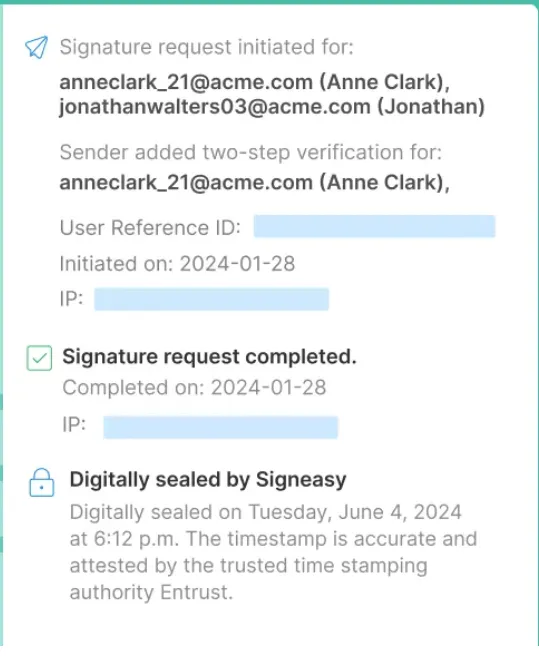
Industry-specific requirements
Certain regulated industries have additional requirements.
For example, according to the U.S. Food and Drug Administration guidance, electronic signatures in FDA-regulated industries must include the printed name of the signer, the date and time of signing, and the meaning of the signature (such as "author" or "approver").
The signature must be permanently linked to the record it authenticates to prevent falsification. Biometric-based signatures must use unique and unchangeable characteristics like fingerprints or iris scans.
Other industries follow their own electronic signature regulations. In finance, rules from agencies like the SEC and FINRA ensure records remain verifiable and unaltered. Healthcare organizations must meet HIPAA standards that protect patient data and verify signer identity.
Public sector workflows, especially in regions like the EU and India, rely on frameworks such as eIDAS Qualified Electronic Signatures (QES) or the IT Act to confirm authenticity and maintain long-term validity.

Why electronic signatures are more secure than wet signatures
Traditional wet signatures (those signed with pen and ink) have been the standard for centuries. We trust them because we've always used them. But familiarity doesn't equal security. In reality, handwritten signatures are surprisingly easy to compromise.
Anyone with steady hands and practice can forge a wet signature. Paper documents can be altered after signing, photocopied to hide changes, or simply destroyed to eliminate evidence.
When you sign with a pen, there's no automatic record of when you signed, where you were, or whether you were the actual person holding that pen. Verifying a disputed signature requires expensive handwriting analysis (a process that can take weeks or months), and even then, the results aren't always conclusive.
Electronic signature security changes this entirely. Secure electronic signature platforms provide multiple layers of protection:
- Encryption protects documents during transmission and storage
- Multi-factor authentication confirms the signer's identity before document access
- Detailed audit trails record timestamps, IP addresses, and device information
- Tamper detection immediately flags any changes made after signing
A forged wet signature might go undetected indefinitely, but attempts to alter a digitally signed document trigger instant alerts. Electronic signature security features in the USA are specifically designed to meet ESIGN Act requirements and industry regulations.
Also read: Best electronic signature solution
In short, electronic signatures are more secure, because
- Wet signatures can be forged or altered easily, and the forge signature penalty can be severe.
- Paper lacks proof of time, place, or signer identity.
- Handwriting verification is slow and unreliable.
- eSignatures add encryption, MFA, audit trails, and tamper alerts.
- Any post-signing change triggers instant detection.
Although many organizations still worry about risks like forgery or unauthorized access, let's understand why these concerns exist.
Common security concerns about electronic signatures
Despite the advantages of electronic signatures, security concerns still hold some organizations back. Are these worries justified? Let's examine the most common fears and what protects against them.
Strengthening electronic signatures with security and authentication measures
Having robust electronic signature security features isn't enough anymore. Organizations must actively implement and maintain these protections to keep documents secure.

A passive approach leaves gaps that attackers can exploit. Strengthening your eSignature security requires layered defenses, proper vendor oversight, and ongoing vigilance.
1. Layer multiple security measures
Relying on just one security feature leaves your documents vulnerable. Instead, secure electronic signature platforms combine multiple safeguards to create layers of protection.
When you pair encryption with multi-factor authentication, you build in redundancy — if hackers breach one layer, the others keep your documents safe.
Organizations should enable biometric verification for high-value contracts, require knowledge-based authentication for sensitive HR documents, and use time-stamping for all legal agreements. The combination makes unauthorized access exponentially more difficult.
2. Maintain oversight of IT service providers
Many organizations rely on third-party eSignature vendors to handle their signing workflows. According to FDA guidance on electronic signature security, sponsors must oversee IT providers through formal agreements that cover system validation, data access rights, and security protocols.
The FDA can inspect these providers directly if they assume regulatory obligations under their contracts. Your vendor agreement should specify:
- Who owns the data and audit trails
- How security breaches will be reported and handled
- Validation requirements for software updates
- Access controls for vendor personnel
- Data retention and deletion procedures
Verify that your vendor maintains relevant certifications such as ISO 27001, SOC2, and compliance with industry-specific regulations like HIPAA, GDPR, and IRS guidelines.
Don't assume your vendor handles everything automatically. Regular audits of vendor security practices help catch vulnerabilities before they become problems.
Also read: Best electronic signature software
3. Tailor security to document risk levels
Not all documents need the same level of security. A company-wide announcement, for instance, requires far less protection than a merger agreement.
Electronic signature security features in the USA allow organizations to configure authentication requirements based on document sensitivity. Low-risk documents might need only email verification, while contracts involving financial transactions should require multi-factor authentication and biometric confirmation.
Creating tiered security policies prevents both under-protection of sensitive documents and over-complication of routine signing tasks.
4. Monitor and update continuously
Cyber threats evolve constantly, and yesterday's strong protection may have today's vulnerabilities. Schedule quarterly reviews of your eSignature security settings, audit trails, and access logs.
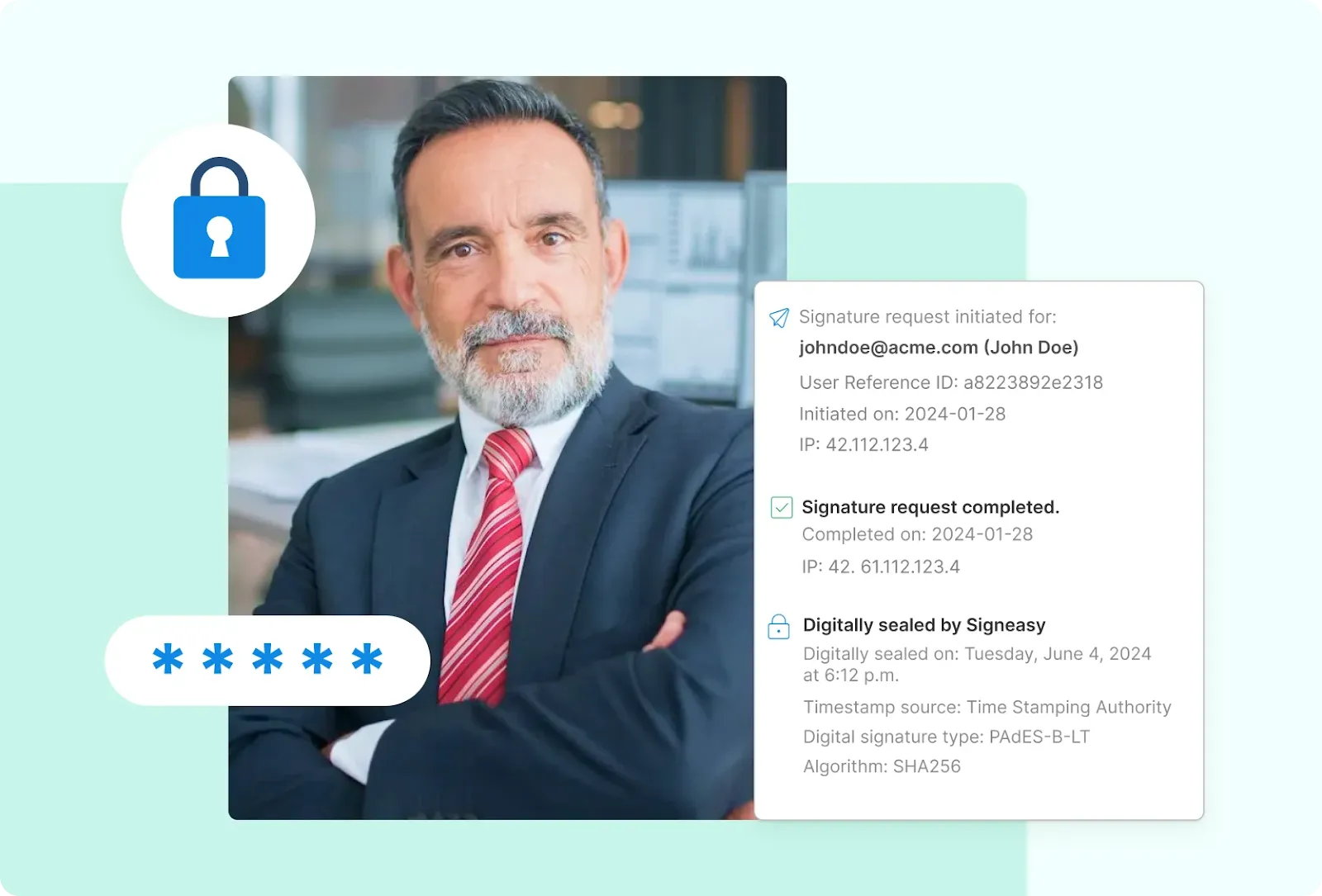
Watch for unusual signing patterns like multiple failed authentication attempts or signatures from unexpected locations that might indicate compromised accounts.
Software updates from your eSignature provider often include security patches. Apply these promptly rather than delaying for convenience. The gap between patch release and installation is when systems are most vulnerable.
Organizations that treat eSignature security as an ongoing responsibility rather than a completed task maintain the strongest protection for their documents and signers.
This level of vigilance only works when security isn't an afterthought — it has to be woven into the fabric of how your eSignature system operates.
Strengthening eSignature security
- Combine encryption, MFA, and biometrics for layered protection.
- Audit vendors and confirm compliance certifications.
- Match security levels to document sensitivity.
- Review settings and logs regularly to prevent breaches.
- Keep security practices active, not static.
Or simply use Signeasy — secure, compliant, and ready out of the box.
The importance of a security-first approach to eSignatures
Security can't be something you tack on later when setting up electronic signatures. It needs to be baked in from the beginning. Companies that get this right from the start end up with systems that actually protect data, stay compliant, and win user trust.
For example, the FDA's stance on electronic signatures shows why getting security right matters. Back in March 1997, they established 21 CFR Part 11, which says electronic records and signatures count the same as paper records and handwritten signatures when they meet certain security standards.
The FDA calls secure electronic signature systems "trustworthy, reliable, and generally equivalent" to traditional methods for clinical work and regulated industries.
Around the same time, the International Organization for Standardization (ISO) introduced information security frameworks that would later evolve into ISO/IEC 27001, now a global benchmark for secure data management and electronic recordkeeping.
A lot has changed since the FDA's previous guidance came out in August 2003. Features like automated timestamps, detailed audit trails, and strong encryption used to be extras. Now they're just part of what you'd expect from any decent platform.
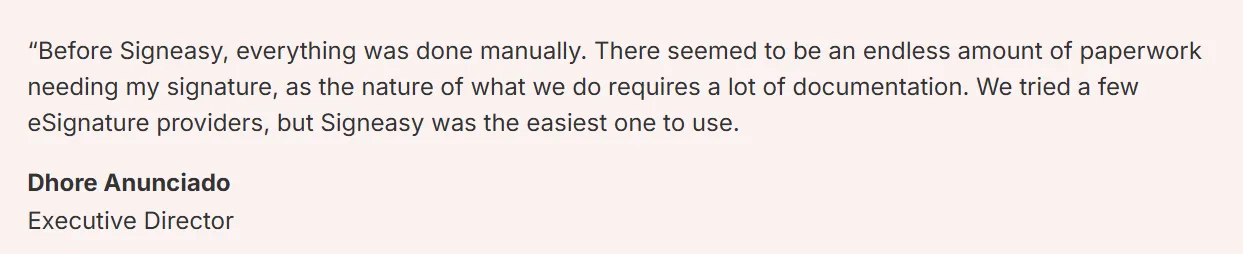
San Diego Eye Bank shows what this looks like in practice.
Since 1959, this healthcare organization has facilitated more than 100,000 corneal transplants worldwide — managing sensitive medical records, lab approvals, and patient agreements every day.
Executive Director Dhore Anunciado noted that documentation in healthcare demands both usability and strict regulatory compliance.
When evaluating eSignature tools, ease of use mattered, but security and data protection came first.
The platform had to:
- Protect patient and laboratory records
- Support secure collaboration among teams and board members
- Meet healthcare compliance requirements
They needed a platform (like Signeasy) where security was non-negotiable.
Once those needs were met through Signeasy, efficiency followed naturally, with Microsoft Teams integration and faster approvals.
Putting that mindset into practice means developing clear procedures for managing access, verifying data, and maintaining compliance.
How to ensure the security of your electronic signatures
Implementing electronic signature security features is just the starting point. Maintaining that security requires ongoing attention and proper controls.
Organizations should actively manage who can access documents, verify data integrity, and ensure audit trails remain intact.
1. Control access from the start
Unauthorized changes must be prevented through robust access controls. Organizations should implement role-based permissions that limit who can view, edit, or sign specific documents based on job function and clearance level.
SOHAR Port and Freezone in Oman faced this challenge when managing contracts across multiple departments.
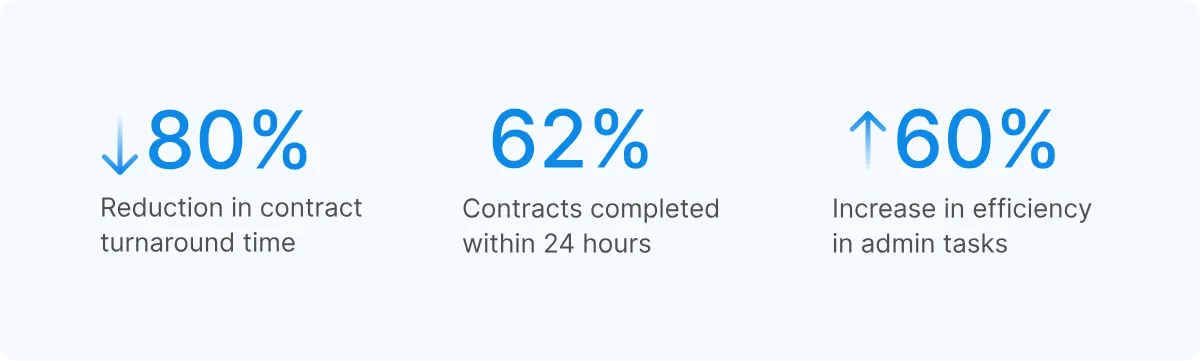
Their manual processes left physical documents vulnerable to unauthorized access and security breaches. After implementing secure electronic signature solutions with single sign-on capabilities, they gained:
- Centralized control over user access
- Efficient permission management by the IT team
- Clear documentation of every action, creating transparency about who signed what and when
2. Validate data transfer and storage
Electronic signature security in regulated environments requires that data transfers to repositories be validated and contemporaneous (occurring at the same time as the signing event).
Choose platforms that automatically timestamp all actions, encrypt data during transmission and storage, and maintain tamper-proof audit trails.
3. Review security regularly
Set periodic reviews of your security measures to stay protected:
- Remove access for former employees immediately
- Update authentication requirements as threats evolve
- Verify that your platform's security features align with current regulations and best practices
With strong protections in place, industries worldwide are putting eSignatures to work.
How eSignatures are being used today
According to the Cloud Signature Consortium's 2025 market report, companies using eSignatures see 70-80% better efficiency in their business processes. Banks have cut scanning errors by 92% after making the switch.

Source
Who's leading adoption:
- Financial services (77%): Banks rely on qualified electronic signatures for loan agreements, deposit contracts, and customer onboarding. Strong security features let these institutions process transactions remotely while staying compliant with regulations.
- Public sector (62%): Government agencies in multiple countries now use eSignatures for tax administration, visa applications, and citizen services. In the European Union, the eIDAS regulation requires public administration to accept qualified electronic signatures in digital processes.
- Healthcare (49%): Medical facilities use secure electronic signatures for patient consent forms, electronic prescriptions, and medical records. Telemedicine platforms, especially in Africa, South America, and Asia, depend on eSignatures to verify treatment plans for patients in remote areas.
- Telecommunications and e-commerce (25% and 19%): These industries have built eSignatures directly into customer onboarding and contract workflows.
Where growth is heading:
Business-to-business relationships are seeing the fastest growth (37% of survey respondents), with business-to-consumer transactions close behind at 36%.
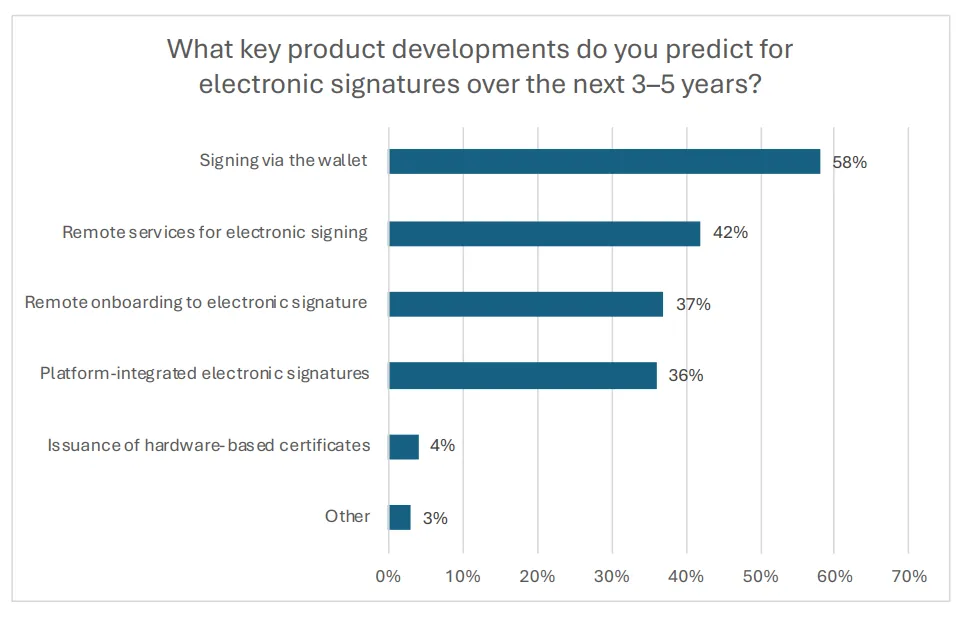
The Cloud Signature Consortium found that 58% of industry professionals expect signing via digital wallets to be the biggest innovation, while 42% anticipate growth in remote signing services.
Source
Real estate, education, and insurance have jumped on board quickly too:
- Universities use eSignatures for student contracts and research agreements
- Insurance companies have streamlined claims processing and policy signing
- Companies increasingly rely on electronic signatures for insurance to accelerate underwriting, reduce paperwork errors, and securely manage policy documents online.
The security features built into these platforms make high-stakes transactions viable by protecting document integrity and verifying signers throughout the process.
What we're seeing is a fundamental shift. Secure electronic signature technology has gone from being a nice-to-have convenience to a business necessity that speeds up transactions, cuts costs, and keeps companies compliant across borders.
Benefits of using secure electronic signatures
Electronic signatures let you do more business without hiring more people to handle paperwork. Here's a breakdown of their top benefits.
1. Speed and efficiency gains
Organizations implementing secure electronic signatures see dramatic reductions in transaction times.
Eversendai, a global construction and engineering company operating across multiple time zones, experienced remarkable results after adopting Signeasy's eSignature solution:
- Nearly 69% of their contracts were completed within the first two days, a critical improvement for keeping projects on schedule and clients satisfied.
- The sequential signing feature streamlined approval workflows across departments from IT to procurement, eliminating bottlenecks that previously caused delays.
GMR Cargo saw similar transformation. Before implementing eSignatures, their CEO's approval process for critical documents took nearly a week as executives physically brought stacks of papers for signing.

After adoption, document turnaround times dropped to approximately one day, enabling faster decision-making across operations, IT, and security departments.
2. Cost reduction and sustainability
Electronic signature security eliminates expenses tied to paper-based workflows:
- Printing and courier services
- Physical storage space
- Administrative overhead
Organizations also contribute to environmental sustainability by reducing paper consumption and carbon emissions from document transportation.
3. Enhanced privacy through selective disclosure
Advanced electronic signature security features now incorporate selective disclosure capabilities. According to the European Telecommunications Standards Institute, selective disclosure "empowers the owner of data to disclose only certain parts of a larger data set, in order for the receiving entity to obtain only such information as is necessary."
Modern platforms use techniques like multi-message signatures and zero-knowledge proofs to ensure presentations cannot be linked to the same identity without authorization. These methods protect signer privacy while maintaining verification integrity.
4. Improved stakeholder experience
Icelandair's transition from a complex Icelandic-only digital signature system to Signeasy enabled their global executives, board members, and partners to sign critical documents within minutes from any device.
Suggested read: Electronic signature vs. digital signature
The intuitive experience significantly enhanced both employee satisfaction and partner relationships. Secure electronic signatures benefit everyone involved in the transaction.
These benefits can be measured in hours saved, costs reduced, and relationships strengthened. They show why organizations worldwide continue accelerating their adoption of secure electronic signature solutions.
Making electronic signature security work for your organization
With the right security measures in place, eSignatures are just as secure as traditional signatures. They offer several benefits, such as the convenience of signing documents online anywhere, anytime, and saving time and money compared to traditional methods. For example, users can sign PDF online to complete contracts, agreements, or other important documents securely and efficiently.
Selecting a platform that meets your security needs is essential if you consider using electronic signatures, and many businesses rely on trusted digital signature providers for secure, compliant solutions. Make sure to research companies thoroughly and read reviews before making your decision. Read IDC’s considerations while buying an eSignature and contract workflow software.